Understanding Stressers and DDoS-for-hire Services
Discover the role of stressers in modern network resilience testing.
What is a Stresser?
Online services designed to test the resilience of servers under
load called Stresser. They are specifically used to simulate overload attack attacks to check the protection of websites and servers. However,
some users exploit stressers to launch unauthorized overload attack attacks on sites
and applications, which is considered prohibited.
The ip stressers industry involves renting out such services, allowing users
to initiate attacks on selected targets. This type of service often attracts attention due to its controversial nature,
and it is essential to understand all legal aspects and potential risks.
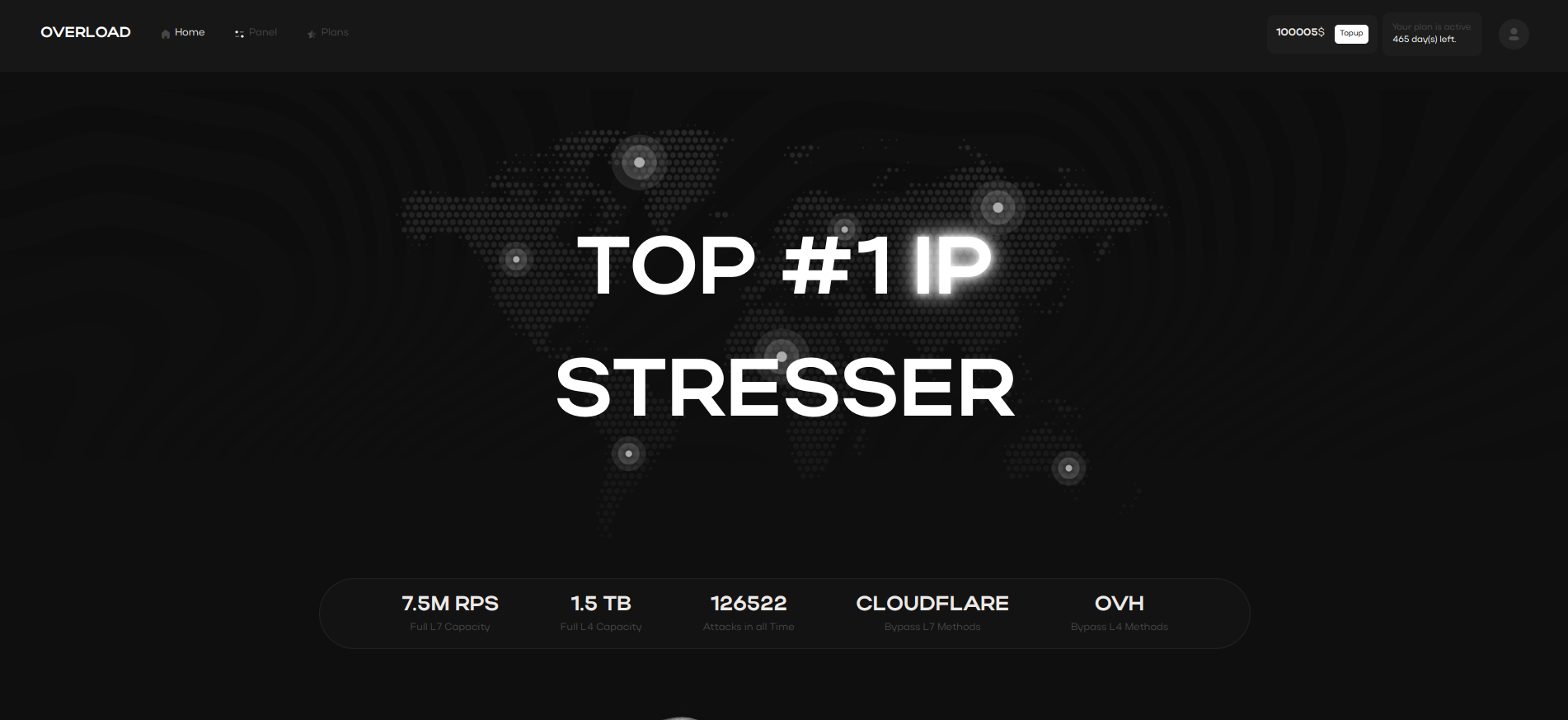
Stresser Techniques: IP Spoofing
Network Layer 4 (L4) attack methods, commonly utilized in IP stressers, selected specific network protocols to overwhelm servers.
One popular technique is source obfuscation, where the attacker’s real IP address is hidden, making it difficult to trace.
These L4 methods and source obfuscation tactics are frequently applied to bypass basic barrier systems protections
and effectively simulate high traffic loads on a selected server.
Amplification Methods in Stresser Services

address spoofing attacks can be enhanced through various reflection-based techniques, such as CLDAP, DNS, NTP magnification.
These methods allow attackers to send small signals and receive significantly larger replies, amplifying the attack’s impact.
By using address spoofing tactics, the attack origin is masked, making it challenging to trace
and prevent the traffic from overwhelming the target’s server structure.
- DNS reflection method
- NTP boost method
- CLDAP amplification